Home/Complimentary Vulnerability Testing
Performing a vulnerability assessment involves identifying, classifying, and suggesting mitigation activities for security weaknesses in an organization’s IT infrastructure. During this process network devices, servers, PCs, mobile devices, applications, or any other elements will be evaluated. This assessment provides insights to IT and security risk officers that are critical to prioritizing risk mitigation activities and limiting targeted cyber-attacks. Once your organization’s immediate issues have been addressed, the assessment will provide you with guidance on how you can make meaningful long-term improvements to your security posture.
Coronavirus-related cyber threats are spiking as hackers exploit the global pandemic to have more targeted engagement with users. These attacks typically come in the form of a seemingly legitimate communication and prompt users to click links or download attachments that contain important new pandemic related information. Among our clients, we have seen an increase in malicious emails of 156% from February to March. A vulnerability assessment will help you understand the efficacy of a potential attack as well as your ability to identify and react to such threats.
Upon completing your Vulnerability Assessment, we will present you with a detailed report and a dashboard. The vulnerabilities are ranked using the industry standard Common Vulnerability Scoring System (1.00-10) and will be categorized as Critical, High, Medium, or Low. The scoring system provides an objective way of comparing the actual business risk for the different vulnerabilities. Additionally, for each risk uncovered, the report will suggest the appropriate mitigation activity which you will often be able to execute with the resources you already have available. The Exelegent team is also accessible to provide guidance or fix these vulnerabilities directly.
View our anonymized report examples:
Scan Dashboard #1
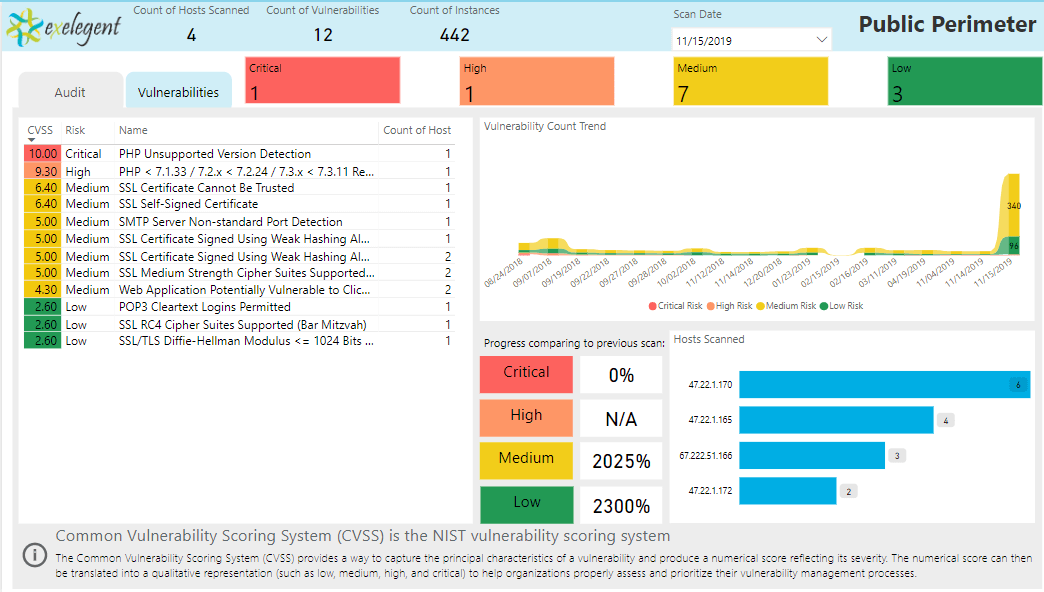
Scan Dashboard #2
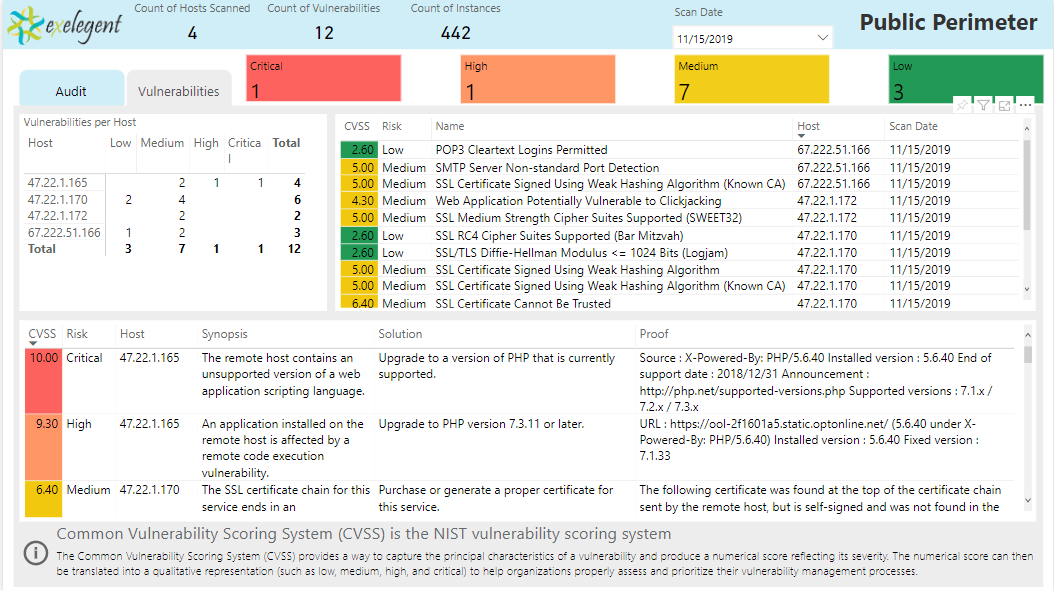
We want you to know that we are in this fight together. Exelegent has made a commitment to tackle security challenges of modern businesses.
Protection and prevention are key. We offer you our resources such as time, staff, hardware, and software, because your security is our priority!

Exelegent is pleased to announce a strategic alignment with ZENEDGE, a leading global provider of Cloud-based cybersecurity solutions for Web Application Firewall (WAF), DDoS mitigation and Artificial Intelligence.

Office 365 is the same Office you already know and use every day. And then some. Because Office 365 is powered by the cloud, you can get to your applications and files from virtually anywhere — PC, Mac, and tablets — and they’re always up to date.

Passwords are used for various purposes. Some of the more common uses include: user level accounts, web accounts, email accounts, screen saver protection, voicemail password, and local router logins.